Whats Tailscale ?
Published on: 2025-08-27 14:04 Author: Jon Brookes
 What is tailscale and why should I care ?
What is tailscale and why should I care ?
First of all, lets be clear, Tailscale is not the only way to achieve some of its goals. Other alternatives are Teleport, Twingate, ZeroTier and you can make your own using Wireguard, if you want to try that. For enthusiastic self-hosters, headscale may be used to run 'your own tailscale' service, for the most part and using tailscale client software to connect to it on our onw physical servers.
First and foremost, Tailscale acts as a VPN. It can be much more than that but lets consider VPNs that were traditional prior to at least, the pandemic.
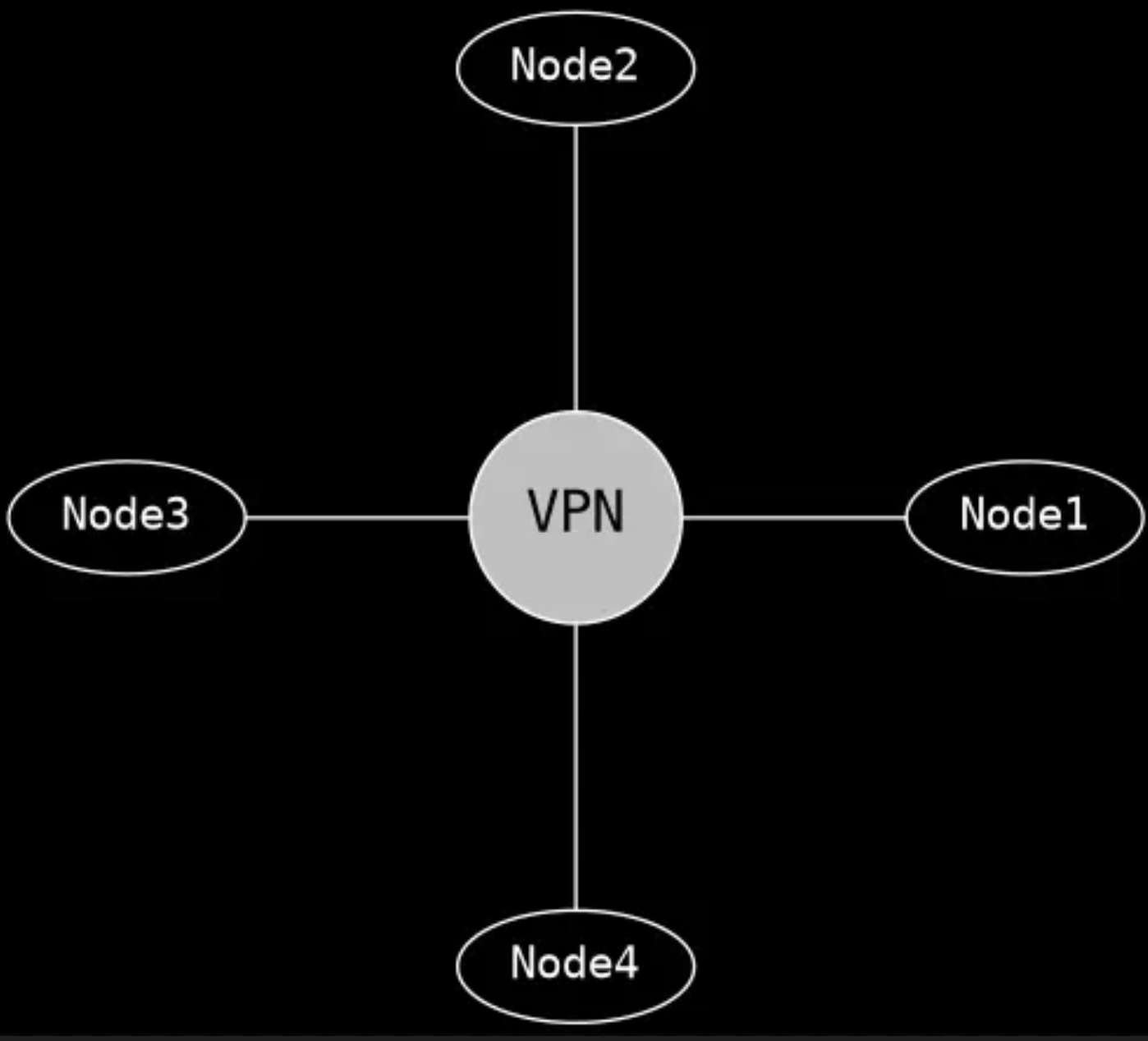 Typically, we would work for a company that on occasions asked us to work from home. When this happened, we started some software on our PC or laptop that created a private connection to servers at work. Lets assume our laptop is Node4 and we need to get a web page from a server in the office on Node1. Our software connects to the VPN which has a public presence on the Internet. Anyone can try to connect to it but only we are allowed to by means of at least a user name and a password. When the VPN checks we are bona fide, it creates a connection for us to and from Node4. Other people may also be connected. They may be on Node2 and Node3. The more people work from home, the more connections are made. It wont be long however until the VPN becomes over loaded as it has to relay every single connection, every single client and service request. This so called 'hub and spoke' architecture served us well until we started to work remotely as much as we do today.
Typically, we would work for a company that on occasions asked us to work from home. When this happened, we started some software on our PC or laptop that created a private connection to servers at work. Lets assume our laptop is Node4 and we need to get a web page from a server in the office on Node1. Our software connects to the VPN which has a public presence on the Internet. Anyone can try to connect to it but only we are allowed to by means of at least a user name and a password. When the VPN checks we are bona fide, it creates a connection for us to and from Node4. Other people may also be connected. They may be on Node2 and Node3. The more people work from home, the more connections are made. It wont be long however until the VPN becomes over loaded as it has to relay every single connection, every single client and service request. This so called 'hub and spoke' architecture served us well until we started to work remotely as much as we do today.
Mesh networks, of which Tailscale is one have been around for a while but have taken the lead on this model as they permit clients and nodes to connect directly to each other. It sounds like magic but it is not. Yet it overcomes the above bottle neck in performance and it does something else, similar to traditional VPNs. It allows us to protect our servers and client workstations or laptops from unwanted attention on the ever increasing hostile attacks on the Internet.
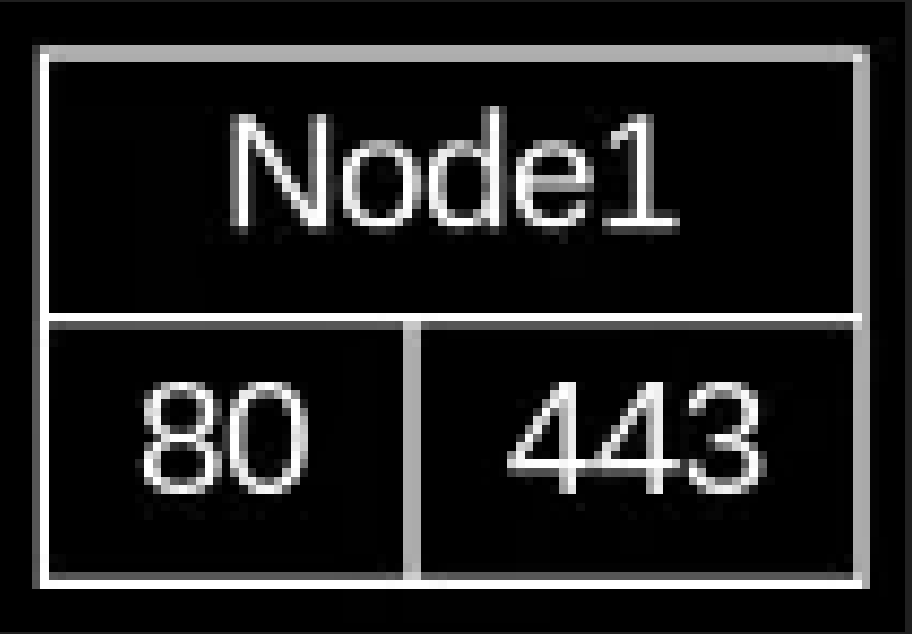
Lets assume we are a self hoster, running our VPS in the cloud. We will call this Node1. From the outside, it must expose 2 ports for our web pages to be visible - 80 and 443. We need 80 for LetsEncrypt to work and for some clients to connect on this to be then redirected to the secure(er) port 443 that becomes encrypted.
What do we do when we need to SSH to this server in order to update it, add new pages, configure new software, if we only allow web page traffic ? SSH needs say, port 22 opened up. Now hackers can attack this port and try to guess our password, even if it is NCC-1701 the number of the starship Enterprise back in the late 1960s and on repeat for ever afterwards. So how do we allow this and other ports access for us to be able to do our work ?
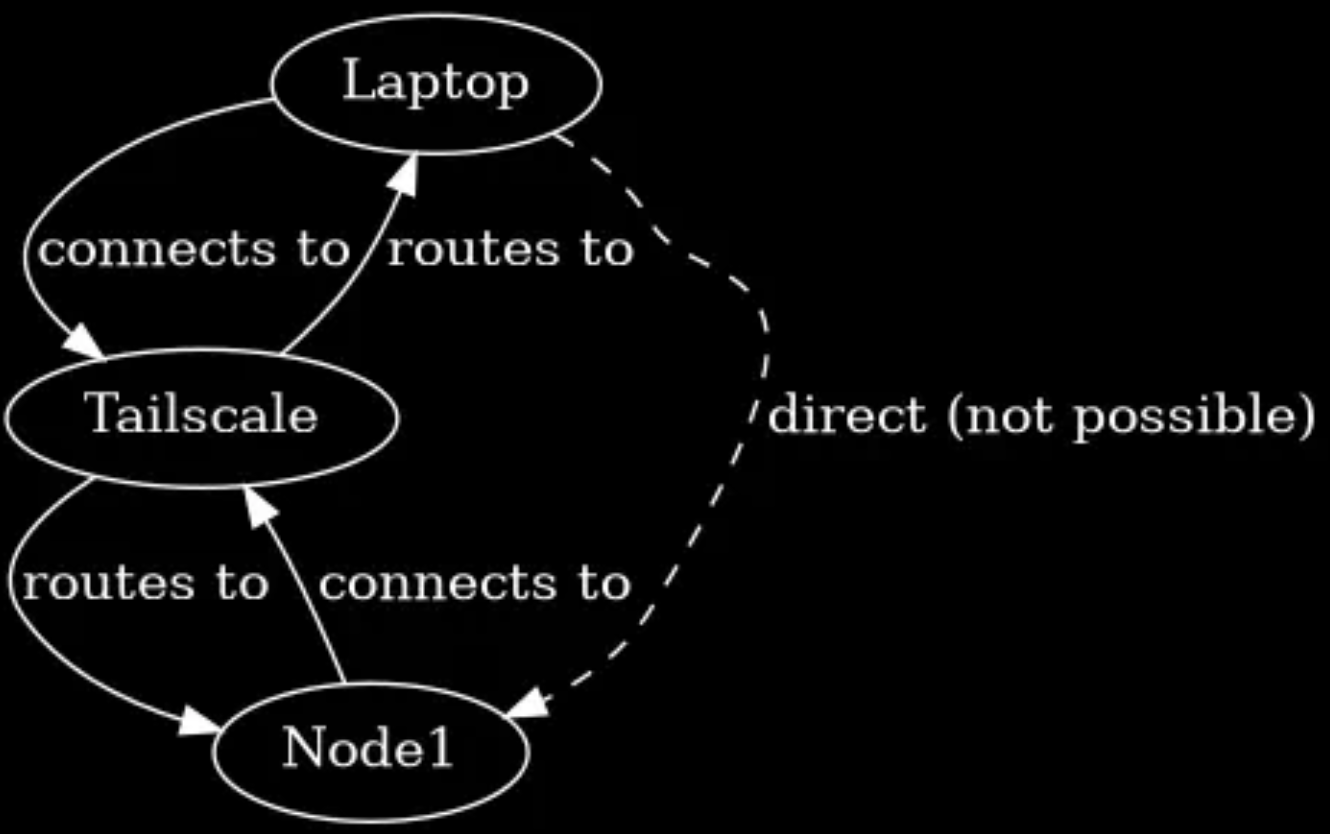 Ahead of time, we set up an account with Tailscale on their 'forever free' tier and download and installed the open source tailscale client on our laptop and our server 'node1'. When each are logged in to Tailnet, the Tailnet server permits both the laptop and the host, node1 to connect to Tailscale. Initially, there is no possibility of a direct connection from our laptop to Node1. However when we try to connect to Node1, the tailscale software works out what we are doing and it creates a connection for us between the two. It acts as a sort of 'in-between' or 'operator' that makes the physical location of both parties manifest to each other. Tailscale does this for you in the background. All you need to to is run an
Ahead of time, we set up an account with Tailscale on their 'forever free' tier and download and installed the open source tailscale client on our laptop and our server 'node1'. When each are logged in to Tailnet, the Tailnet server permits both the laptop and the host, node1 to connect to Tailscale. Initially, there is no possibility of a direct connection from our laptop to Node1. However when we try to connect to Node1, the tailscale software works out what we are doing and it creates a connection for us between the two. It acts as a sort of 'in-between' or 'operator' that makes the physical location of both parties manifest to each other. Tailscale does this for you in the background. All you need to to is run an ssh command to Node1. It does all that magic in the background for us. 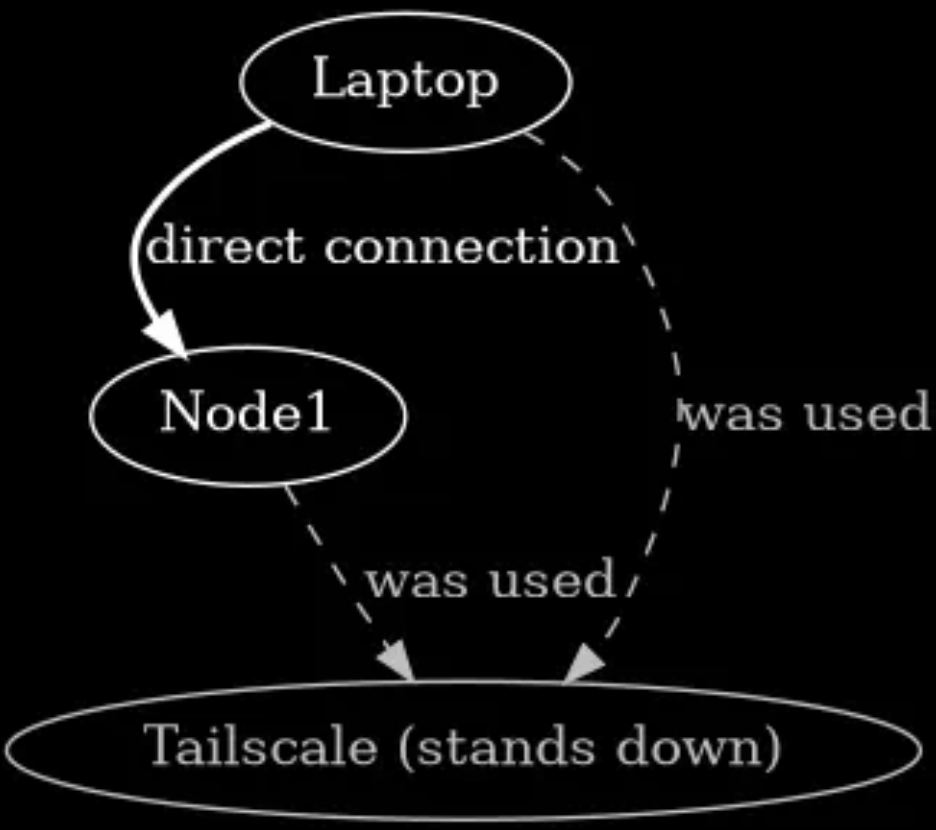 When Tailscale has done its job, it stands down, having created a connection between our laptop and our server Node1. It does this with secure encryption with Wireguard, which is a modern, secure protocol that is widely used today.
When Tailscale has done its job, it stands down, having created a connection between our laptop and our server Node1. It does this with secure encryption with Wireguard, which is a modern, secure protocol that is widely used today.
From here on in, our connection not only seems to be but actually is direct from our laptop to our server, Node1 and without ever needing to open up an extra port that hackers could try to connect to.
But there is more. Tailscale and others like it break the old 'hub and spoke' model and take away what has become a massive bottle neck for SMEs and big tech alike. Indeed it is cheaper for the self-hoster too.  Wireguard allows us to connect multiple systems together, be they a laptop, a server, even containers that have a tailscale client installed, verified and logged in to our tailnet account.
Wireguard allows us to connect multiple systems together, be they a laptop, a server, even containers that have a tailscale client installed, verified and logged in to our tailnet account.
When we say 'connected' what we mean is that each node periodically talks to the Tailscale service to see if anyone needs to connect with them, at which point, it makes the connection, like an old fashioned telephone exchange or like in the Matrix and the 'operator' for it then to step back and allow each node to talk directly with each other via the shortest possible route.
We have established not only secure point to point connections but have done so in a way that is highly efficient and 'feels like' being on the same network. There is no central VPN to go through all of the time, only for initial connections.
There after, the tailscale clients keep direct connections open and 'alive' for as long as is needed. This makes file and data transfer between each node on our 'tailnet' network as fast and efficient as possible.
This all said, the technology behind tailscale 'tailnet' networks can fail to establish direct connections betwween some clients. However this is only in certain 'edge' cases. One such is where strict firewall rules block certain types of traffic over 'UDP'. So what happens if you find yourself behind such a firewall ? Tailscale services can then fall back to a more traditional 'relay' service. You will still have access to your infrastructure then, even if your unfortunate to have to use such networks.